100% CPU usage when running WSL2 in Check Point Endpoint Security VPN installed environment : r/bashonubuntuonwindows
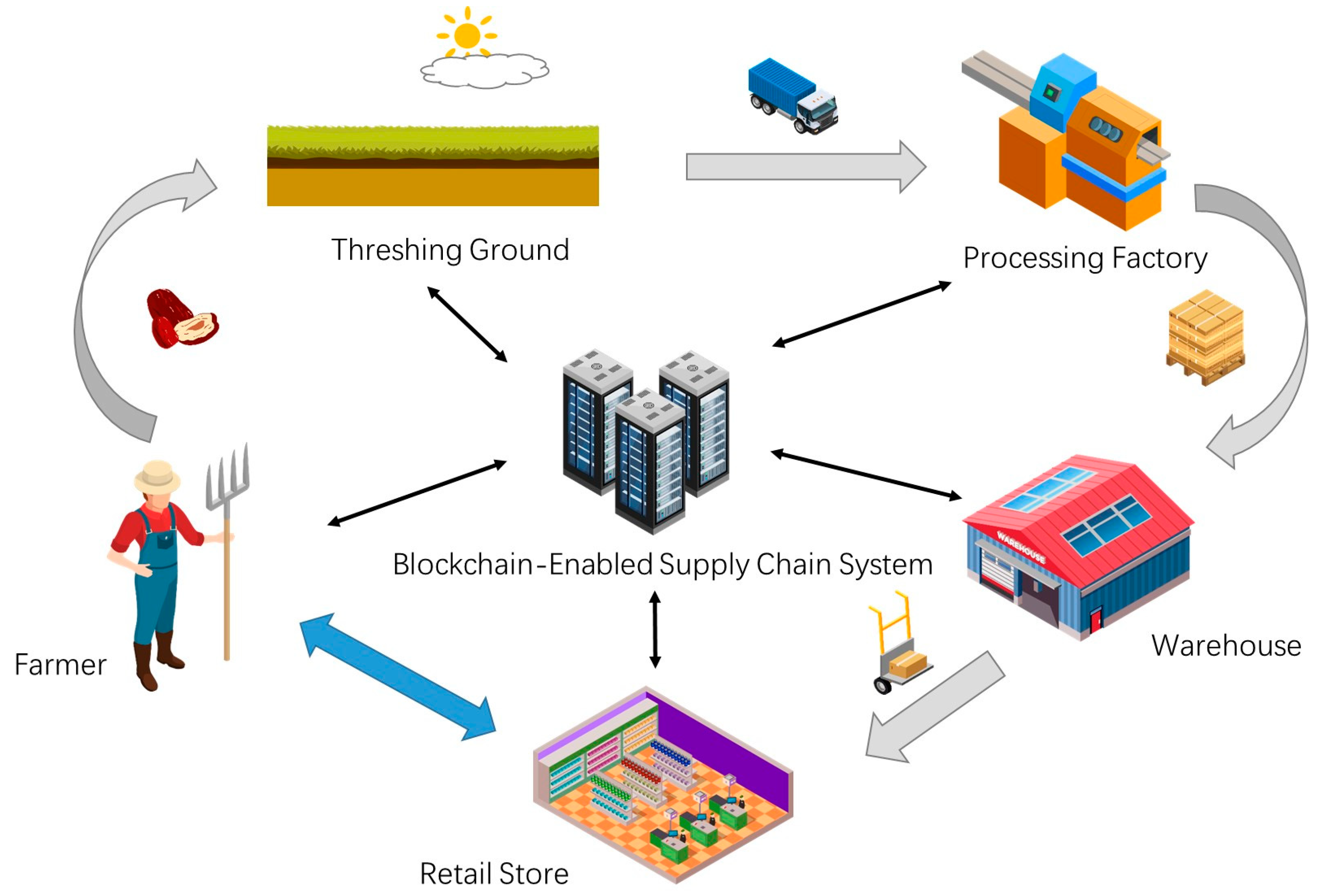
Foods | Free Full-Text | A Novel Blockchain-Enabled Supply-Chain Management Framework for Xinjiang Jujube: Research on Optimized Blockchain Considering Private Transactions

US7987490B2 - System and method to acquire, aggregate, manage, and distribute media - Google Patents